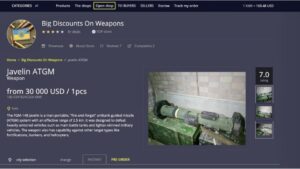
One notable example of technological diversification can be found at this online portal, which offers further understanding...
Uncategorized
The global nature of this type of crime requires a level of cooperation amongst law enforcement agencies...
Drugs lead the pack—weed, pills, some synthetics—but digital goods like hacked logins are gaining, tying into Telegram’s...
This template will give you some ideas on how to surprise your followers. For instance, it’s important...
Use extreme caution when visiting any darknet market and never share personal information. Alphabay, first launched in...
These marketplaces are full of risks (security, legal, ethical issues – all of them). But if you...
This makes it incredibly difficult to find out who you are paying. Following the NYT, the BBC...
These services form the communication backbone for sensitive conversations in high-risk environments. Embarking on a journey through...
Activists, whistle blowers, and journalists also use the dark web to communicate securely with sources and news...
Simple mistakes—such as inadequate operational security practices, sharing identifiable details, or using compromised devices—can quickly compromise anonymity...