
Tor greatly enhances anonymity, but if an attacker controls both the entry and exit nodes, they could attempt traffic correlation to link your identity to your activity. You can also be tracked by logging into personal accounts, downloading unsafe files, or modifying browser settings that expose your digital fingerprint. Using Tor with a VPN adds an extra layer of protection by masking your IP from the Tor entry node. Using the dark web comes with serious risks for users who don’t take proper precautions. Malicious links, phishing traps, and fake sites designed to steal your data are very common. Additionally, while the Tor Browser (the most common tool for accessing the dark web) has some built-in privacy and security features, it’s not 100% safe..
If Something Goes Wrong: Survival Guide
Yes, governments and law enforcement agencies have developed sophisticated techniques to track and investigate illegal activities on the dark web. They can sometimes identify users through other methods, such as monitoring behavior, exploiting vulnerabilities or conducting undercover operations. Tor routes your traffic through three random nodes in different countries. Even if someone intercepts the data, they’ll only see an encrypted stream between nodes – not your real IP.
Accessing the dark web is legal in India as long as you do not engage in illegal activities such as buying drugs or hacking services. When you want to access the dark web, you need a special browser. Popular browsers, like Chrome and Safari, are unsuitable; You need a special dark web browser to open the encrypted dark web while preserving your anonymity. There are several ways to protect your online activities from being tracked.
Install A Virtual Private Network (VPN)
If someone’s caught buying or selling illegal items like credit card numbers or hacked data, they can face serious federal charges—even if it all happened behind an anonymous screen. From real-time alerts vetted by Cyble’s Security Operations Center (SOC) to AI-driven risk tagging, Cyble enables faster, more informed response decisions. Its deep insights into cybercrime forums, compromised card databases, and exposed assets give security teams a critical edge. Lastly, keeping the Tor browser and any security software up to date is important for staying ahead of potential vulnerabilities. By following these tips, individuals can enhance their safety and privacy while exploring the Dark Web. There are various sites on the dark web dedicated to the distribution and discussion of hacking tools, cyberattack services (such as DDoS attacks), and information on data breaches and leaks.
Accessing Onion Sites On Android
It’s the last part of an internet domain name, stated after the last dot. For example, Google.com and PixelPrivacy.com both belong to the “.com” top-level domain. So, even though it does exist on the internet, Google doesn’t index any of these pages or content.
What Is Tor?
It protects your real IP address even if Tor leaks, is easier to set up, and works with most major VPN services. Open the VPN app and connect to a nearby server before launching the Tor Browser, and that’s it! Protecting your personal information should be your priority when using the dark web. Don’t share sensitive details, such as your name, address, phone number or financial information, with anyone.
Should I Use The Tor Browser For Everything?
- Because of these privacy features, the dark web remains a hidden but active part of the internet ecosystem.
- While not mandatory, using a VPN adds an extra layer of privacy and security by hiding Tor usage from your internet service provider.
- Most likely, the native account on your device has full admin permissions by default.
- In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network.
- There are a variety of private and encrypted email services, instructions for installing an anonymous operating system and advanced tips for the privacy-conscious.
- Using a VPN (Virtual Private Network) in tandem with the Tor browser ensures an added layer of security by encrypting your traffic before it reaches the Tor network.
If you want to use Tor privately, you can use either a VPN or Tor Bridges (Tor nodes that are not publicly indexed). Tor users in the USA, in particular, may want to use a VPN, which will be faster and more reliable. Based on Firefox, the Tor Browser lets you surf the clear and dark web. All your traffic is automatically routed through the Tor Network.
Services like Random Chat connects you with random people using the same service. Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations.
Alternatively, bridges can be obtained through other channels, such as sending an email to the Tor Project’s bridge distribution service or via a dedicated Telegram channel. Once obtained, these bridge addresses can be manually entered into the Tor Browser’s configuration. Another circumvention tool integrated into Tor Browser is “Snowflake,” which allows users to connect through temporary, ephemeral proxies, further aiding in bypassing network blocks. The choice of which circumvention method to use often depends on the specific nature of the blocking being encountered.

Step 5: Find Verified Onion Links
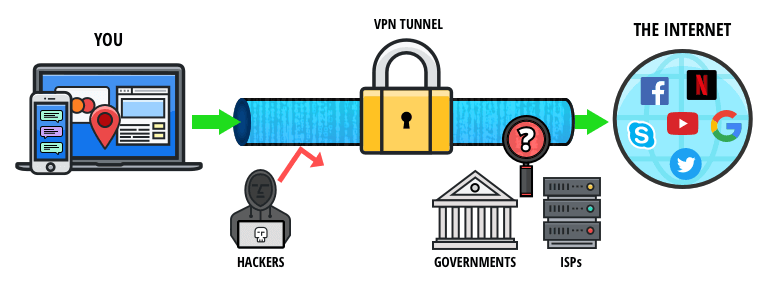
However, navigating this hidden digital landscape in 2025 presents heightened security risks, from advanced cyber threats to targeted surveillance. This guide provides clear, step-by-step instructions to safely explore the Dark Web using Tor, helping you stay protected, informed, and anonymous. Without a VPN, the first server in the Tor network (the entry node) can see your real IP address, and your internet service provider (ISP) can see that you’re accessing the dark web.

While Tor offers anonymity by routing your traffic through a decentralized network of nodes (onion routing), it shouldn’t be your only line of defense for privacy. Malicious actors and government agencies can run Tor nodes, compromising privacy and security. In fact, there have been instances where attackers controlled hundreds of Tor nodes.
If a user visits a website that has implemented Onion-Location using Tor Browser, a purple suggestion pill will appear in the URL bar, displaying “.onion available”. Clicking on this prompt will automatically reload the website and redirect the user to its onion counterpart, providing a more secure and private connection through the Tor network. This feature offers a more direct and potentially more trustworthy way to find the onion versions of legitimate websites. Unlike typical web browsers, Tor Browser uses onion routing, which encrypts and routes traffic through multiple servers around the world to hide your IP address and provide private browsing.
Our Network
Keep yourself informed about the latest security tips and potential risks by following cybersecurity blogs or forums. Keeping your security software up-to-date is vital in protecting your device from threats. Regular updates ensure your antivirus and firewall can detect and block the latest malware. It also adds an extra layer of anonymity, which is particularly important when browsing the dark web. Choose a reputable VPN service with strong encryption and a no-logs policy to ensure maximum privacy. Navigating the dark web can be like exploring a labyrinth — there are hidden treasures but also potential traps.
Commercial Services
Well known for its emphasis on security and privacy, the Tor browser distinguishes itself from mainstream browsers like Firefox or Chrome. Unlike the direct route taken by conventional browsers, Tor employs a series of encrypted servers known as nodes, chosen randomly, to ensure both user and site anonymity. Law enforcement agencies worldwide have grappled with the challenges posed by the Dark Web, attempting to balance the need for online privacy with the necessity of combating criminal activities. If you are looking to read combating crime on the dark web online, many resources and platforms are available that shed light on the ongoing efforts to curb the growing threats of cybercrime.
Avoid sharing personal information, downloading unknown files, and engaging in illegal services. A regular dark web browser will only encrypt your browser traffic; Orbot goes further and encrypts all data in and out of your phone. It is a mobile application that uses your Android or iOS device’s VPN mode to route all traffic through the Tor network. Tor was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag. Tor was designed to protect American intelligence communications online.



