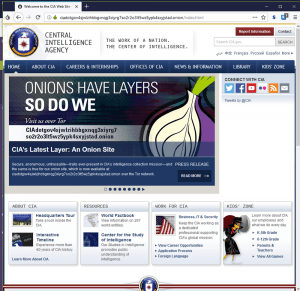
Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Torch is the oldest and largest .onion search engine with more than 1 million .onion sites indexed. Just bear in mind that many of those will be out of date, and using this index will require a lot of discretion, due to its size. This onion site was created as a place for whistleblowers to pass information to journalists. It is a safe haven where anybody with information can share it anonymously and without fear of being tracked.
Why Is Tor So Slow?
They can be easily traced and even prosecuted if they share the information on the surface web. SecureDrop is a site that protects the privacy of journalists and whistleblowers. It allows you to search for images, maps, files, videos, social media posts, and more.
- The Tor Project was initially developed by the US Navy to protect online intelligence communications, before its code was publicly released in 2002.
- It works like any other popular messaging app and even offers Exploding messages that automatically delete after a fixed period of time.
- Their URLs (aka dark web links) have .onion as the domain, instead of the common surface web domains like .com or .net.
- If the BBC is unavailable in your region, you can still reach it through the BBC Tor Mirror.
- A VPN encrypts your online activity and shields private information such as your IP address, providing an additional layer of security and anonymity online.
- Not every visitor is a criminal, but this is where most cybercrimes begin.
Which Is Better — Tor Over VPN Or VPN Over Tor?
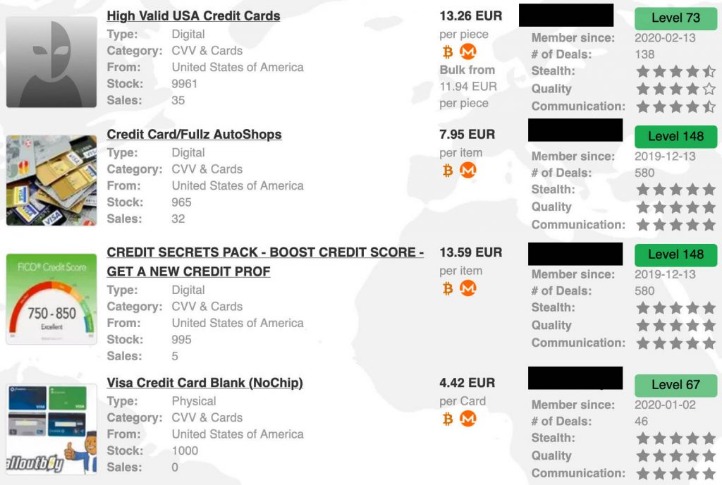
Beyond its directory functions, the platform also serves as a community hub where you can discuss various topics and share your experiences. Its longevity and reputation have solidified its position as a cornerstone of the Dark Web community. We’re back with another video in our Webz Insider video series on everything web data. Learn how to automate financial risk reports using AI and news data with this guide for product managers, featuring tools from Webz.io and OpenAI. Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP.
The Tor Browser routes your internet traffic through a network of servers, making it difficult for anyone to track your online activity. Such operations are facilitated by cybercrime and transnational organised crime treaties which address child sex abuse material and the trafficking of women and children. Forum members distribute media, support each other and exchange tips to avoid police detection and scams targeting them. Another study estimated 53.4% of the 170,000 or so active onion domains contained legal content, suggesting 46.6% of services had content which was either illegal, or in a grey area.
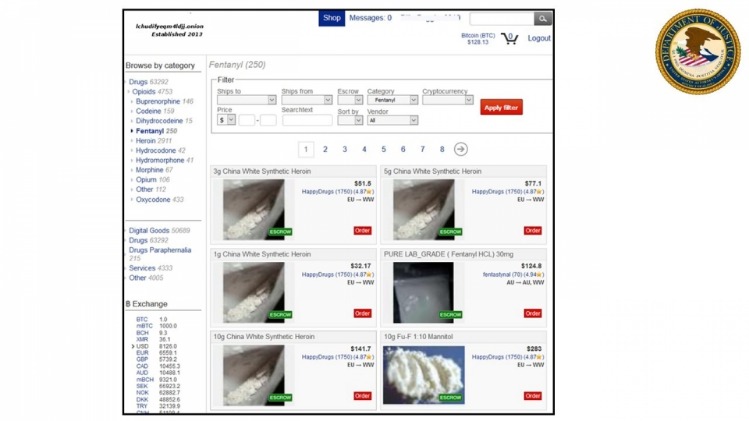
Use Active Monitoring Of Financial And Identity Theft
Prominent organizations like The Guardian, The New York Times, and ProPublica have implemented it. The software requires two-factor authentication to receive what’s been uploaded by the whistleblower and allows two-way communication between the anonymous contact and the media outlet. Borderless news reporting and uncensored media are among the most important and practical uses for the dark web. Bypassing firewalls and other forms of geo-blocking helps people to access news websites and social media they normally wouldn’t be able to — and do so with less fear of recrimination. Swiss based ProtonMail is an encrypted email service that is quite popular with the cryptocurrency community. It’s a paid service, and while it’s extremely secure you will need another email address to sign up, which can leave traces of your true identity without you realizing.
What Are The Best Cryptography Tools For Data Protection In 2025?
In addition, Ahmia and Haystack make every effort to filter out and blacklist sites known to contain harmful, abusive, or illegal content. This makes them a safer (though still not foolproof) option for searching the Dark Web. The nice thing about Ahmia is that it lists .onion sites that want to be found. Many of those sites are listed because their devs have submitted the site directly to the search engine for indexing.
KeyBase combines encrypted messaging with secure file sharing and identity verification. Its dark web version provides the same functionality as the clear web option, while adding Tor’s anonymity layer. Pitch is a dark web-based Twitter/X alternative, providing a secure platform for anonymous discussions and information sharing. Unlike many dark web platforms, it maintains strict content guidelines while protecting user privacy. Founded around 1999 by activists in Seattle, it has since grown to over six million users worldwide. It publishes a newsletter in multiple languages and not only runs onion services for its website but all its email and chat services.
Hidden Answers

With these guidelines, exploring the dark web can be done securely and confidently. By following simple yet crucial safety measures, you can effectively minimize risks and safely satisfy your curiosity about the hidden parts of the internet. For those venturing to the shadier side of the web or those who just want to know their identity is safe, dark web monitoring tools and identity theft protection are a must-have. Typically, you can find dark web URLs through forums, databases, or by talking to others who frequent those sites. Hacking and cybercrime forums on the dark web are spaces for newbie hackers to ask questions, veteran cybercriminals to share their expertise, and buyers to find sellers.
Wofür Werden Onion-Seiten Verwendet?
The .onion site is aimed at individuals that want to share information anonymously with the spy agency but are at the risk of being tracked. Unfortunately, most of the mainstream media today can’t be trusted because it’s rarely unbiased and accurate. The best way to stay up-to-date with the latest happenings is to use an open-source and community-oriented news aggregator like SoylentNews.
Many services that are allegedly offered on the dark web are scams. Some services are genuine; you can get what you want at an agreed fee. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals.
Son was sentenced to 18 months in prison in South Korea; however, the nine-count indictment against him was only unsealed on Wednesday. Child sexual abuse material is rampant online, despite considerable efforts by big tech companies and governments to curb it. And according to reports, it has only become more prevalent during the COVID-19 pandemic. You can also use it for hosting websites which will use your computer as the host server. It also safeguards your data by using the Neutrino protocol to eliminate the use of third-party servers for conducting transactions.

Halo Security Enhances Platform With Custom Dashboards And Reports
- On the other hand, we have Tor2Web, which is a service that helps people who are not yet in the Tor network.
- The dark web contains content that’s only accessible through networks like Tor.
- The best way to stay up-to-date with the latest happenings is to use an open-source and community-oriented news aggregator like SoylentNews.
- As you continue your online journey, keep expanding your knowledge of digital privacy and security.
Riseup is available on the surface web, but its presence on the Tor network extends its privacy benefits by letting you use its services without exposing their real-world identities. You can access encrypted email services through the onion site without getting tracked. It’s maintained by a volunteer-run collective from the USA that protects the platform from malicious attacks and pledges to support social justice and progressive causes.
These websites live on the unindexed, hidden part of the internet known as the dark web. To access the dark web, you need a dark web browser like Tor Browser. And many people use a VPN with Tor, because while the Tor network offers anonymity and privacy, extra security is recommended when accessing the dark web. Using a reliable VPN like ExpressVPN with dark web search engines is essential for protecting your privacy. It hides your IP address, encrypts your internet traffic, and prevents your activity from being traced.
But, honestly, if you are going on the dark just to enjoy free music, we recommend that you go for free torrent platforms on the surface web instead. If you wish to access the snapshots of these websites, just type in the domain name, and you will get the results depending on how many records exist on the website. However, not all books on this site are legally available, so they don’t have copyrights. That means you may violate copyright laws while downloading books, so use a VPN to protect yourself from any legal repercussions if you have a dire need to use it.