Without regulated oversight, buyers risk losing money or, worse, exposing their identities to cybercriminals. A VPN encrypts your traffic before it reaches the Tor network, preventing your ISP from seeing that you’re using Tor. Instead, use disposable email services and end-to-end encrypted communication tools like ProtonMail or Signal. There are several ways to protect your online activities from being tracked.
A VPN automatically encrypts your data as soon as it leaves your device through the VPN server. This means your private information, location, and any communications you send are hidden and protected. That being said, the anonymity offered by the dark web is the perfect breeding ground for criminals from all walks of life and users are advised to browse with extreme caution.
If you choose to explore the dark web, do so ethically and legally to avoid potential risks. Privacy-conscious users, including journalists and political activists, use the dark web to communicate securely, especially in oppressive regimes. Many journalists, whistleblowers, activists, and even government agencies use it for privacy and secure communication. However, some nations have banned or restricted its use due to security concerns. The dark web is often confused with the deep web, but they are different.
Maintaining Security And Privacy
It is crucial to approach the dark web with caution and understand the risks involved. Engaging in illegal activities can lead to severe consequences, and exposing personal information or engaging with malicious individuals can compromise your privacy and security. Dark web encryption allows website owners and users to stay completely anonymous during their engagement. It’s a part of the internet that’s less regulated and more shadowy, for better and for worse.
Stay In Touch With Us

Browsing the dark web puts you at risk of cyberattacks such as DDoS attacks, botnets, and other malware or viruses. By simply entering the wrong URL or accidentally downloading a malicious file, you could install infectious viruses or malware. This can have a detrimental impact on your device or, even worse, expose your personal information. It routes all traffic through Tor, preventing IP leaks and offering stronger protection against tracking.
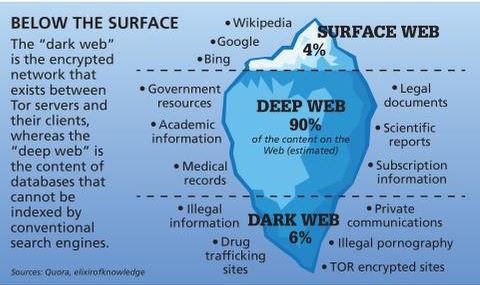
Different Layers Of The Internet
The Dark Web differs from the Surface Web, which is the accessible and indexed part of the internet, in several ways. Users can access websites without revealing their identities, making it attractive to individuals who value privacy. Additionally, the Dark Web offers a marketplace for various goods and services, some of which may be illegal. This hidden marketplace allows for transactions involving drugs, weapons, hacking services, and other illicit activities.
- These risks can be avoided when you are well-informed and know how to protect yourself against them.
- If you need a way to organize as an activist or you want to discuss censored topics with others, my first suggestion is to stick to offline meetups.
- Follow this step-by-step guide carefully to ensure safe, anonymous, and secure access to the Dark Web using Tor.
- The easiest way to access Tor is through a special browser known as the Tor Browser.
Can Tor Browser Be Used For Regular Internet Browsing?
It is a high danger of fraud and theft of identities on the dark web due to the prevalence of unlawful content and crimes there. A virtual private networking (Proxy server) is just a great way to hide your online identity as well as your place whilst allowing you to access the internet securely. Personal and financial information should never be exposed on the dark web either via links from unknown sources. Improve your online health by using long passwords for each account and turning on two-factor login. You can protect your privacy and security when surfing the dark web if you take the proper procedures and retain alert.

How Can I Increase Security While Using Tor?

However, it’s important to note that not everything on the dark web is illegal. Journalists, activists, and individuals concerned about privacy and censorship often use the dark web to communicate securely and anonymously. Nevertheless, caution should always be exercised when venturing into this hidden realm. Dark web sites are hidden by non-indexing, making them completely anonymous. You’ll need a purpose-built browser that uses The Onion Router (TOR) to access dark web content.
Step 2: Installing And Configuring Tor Browser

The dark web contains a wide variety of services and content, some of which skirts or disregards legality. Though the intention and purpose of users on the dark web may vary, the dark web itself is neither good nor bad. Be aware, however, that there are sites for absolutely everything, from the benign to the very illegal. There are some websites you can absolutely get in legal trouble for even visiting, so proceed with the utmost caution.
Where Can I Find Safe Onion Links?

The browser is open-source software that is free to download and enables anonymous communication online. Users’ internet traffic is sent through an encrypted network of volunteer-maintained relays around the world. Tor’s anonymity function is used by everyone from human rights workers and journalists through to drug and arms dealers. The Dark Web refers to a specific section of the internet that exists on an encrypted network, intentionally hidden and accessible only through specialized software. It forms a small part of the Deep Web, a term that encompasses all parts of the internet that are not indexed by traditional search engines.
- It’s designed to offer users complete anonymity and privacy for their online activities, which range across both lawful and unlawful spectrums.
- Accessing the Dark Web can expose you to a range of risks that might not be immediately apparent.
- You could easily use Tor in an attempt to pirate copyrighted content from the deep web, share illegal pornography, or engage in cyber terrorism.
- Use directories like The Hidden Wiki or Dark.fail, which list verified and regularly updated onion links.
- A study, Into the Web of Profit, conducted by Dr. Michael McGuires at the University of Surrey, shows that things have become worse.
Instead of relying on traditional domain name system (DNS) servers, onion websites use cryptographic keys and hashes to generate their URLs and establish connections within the Tor network. With the Tor network connection established, you can now browse and access websites with .onion addresses, which are exclusive to the Dark Web. Simply enter the .onion URL in the Tor Browser’s address bar, and the browser will retrieve the requested website from the Dark Web.
These websites use special encryption protocols and are accessible only through anonymizing tools like the Tor Browser. By following these steps, you enter the Dark Web with more confidence and preparedness. Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be. Stay vigilant, trust your instincts, verify sources, and prioritize your security to make the most of the anonymity these networks provide. I2P is an anonymous overlay network designed primarily for peer-to-peer applications. The Dark Web’s cornerstone is built upon specialized anonymity networks and protocols that allow users to access hidden services without directly revealing their identity or location.
However, engaging in illegal activities on the dark web is against the law. The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. Though not entirely shoddy, the dark web has a reputation for hosting illegal activities.
By following this step-by-step guide and exercising caution, you can access the Dark Web securely and explore this hidden part of the internet responsibly. If you have a legitimate or viable need to access the dark web, you’ll want to make sure you stay safe if you decide to use it. That said, anonymity comes with a dark side since criminals and malicious hackers also prefer to operate in the shadows. For example, cyberattacks and trafficking are activities that the participants know will be incriminating.
For individuals living under oppressive regimes or anyone needing to communicate away from the watchful eyes of surveillance, the dark web is a valuable tool. A substantial portion of users turn to the Tor browser for its promise of anonymity, while others seek the additional security it provides. Curiosity about what the dark web has to offer also drives about one-third of its users. Unlike typical web browsers, Tor Browser uses onion routing, which encrypts and routes traffic through multiple servers around the world to hide your IP address and provide private browsing.



