
Put simply, the deep web is all the information stored online that isn’t indexed by search engines. You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look. Specialized search engines, directories, and wikis can help users locate the data they’re looking for. Because dark web pages generally aren’t indexed, you can’t find them using traditional search engines, but some search engines like DuckDuckGo may help you navigate the dark web more easily. The Hidden Wiki is a directory hosted on the clear net (also called the “surface web”) that contains a list of .onion links for many of the best dark web websites.
First, Install A Reliable VPN
Although websites can’t identify you and ISPs can’t decrypt your internet traffic, they can see that Tor is being used. Tor is a network of volunteer relays through which the user’s internet connection is routed. The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous. Among the many benefits of using a VPN vs a proxy or Tor is that it provides full encryption for all the data you send and receive online.
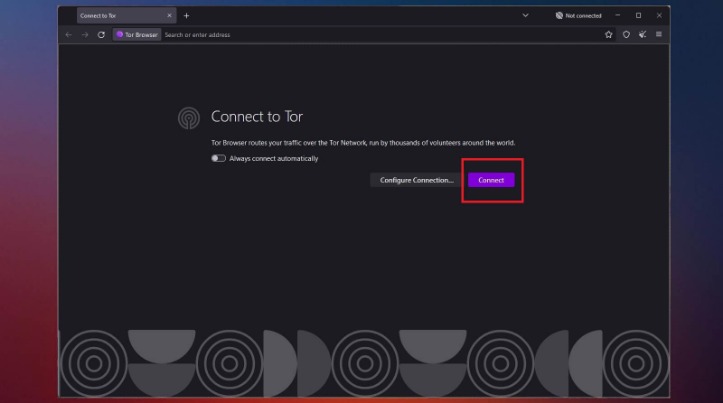
Is It Illegal To Visit And Use Dark Websites?
By using a VPN to connect to Tor — a special browser designed to access the dark web — you can securely access the dark web using a technique known as Tor-over-VPN. Without a VPN, your ISP or network administrator may be able to detect, monitor, or block dark web access; Tor-over-VPN provides an extra layer of privacy. The dark web is a murky part of the internet that isn’t accessible via a normal browser — and can be dangerous to visit if you don’t know what you’re doing. We’ll show you how to access and browse dark web sites, and how using a VPN to encrypt your connection can help you visit the dark web more securely.

Minimize Or Rescale Your Tor Browsing Window
These sites aren’t just important resources; they’re like lifelines used to serve readers living under oppressive regimes. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. Everything you find on the dark web is not necessarily illegal.
- Tor anonymizes by bouncing traffic through relays; VPN encrypts and routes through a single server.
- If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security.
- I’ve always been kinda curious myself about how to access it, how to navigate around it, and how to keep yourself safe when browsing.
- So not only is your web activity hidden, but you can mask your IP address by connecting via a wide range of global VPN server locations.
- If you want to use Tor privately, you can use either a VPN or Tor Bridges (Tor nodes that are not publicly indexed).
- The best way to find out is to check the “Have I Been Pwned” (HIBP) website.
Legitimate Use Cases For The Average User
Your account must be older than 4 days, and have more than 20 post and 10 comment karma to contribute. When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use.
Roundup – Best VPNs For The Dark Web

The final relay before your traffic goes to the destination website is known as the exit node. The exit node decrypts your traffic and thus can steal your personal information or inject malicious code. Additionally, Tor exit nodes are often blocked by websites that don’t trust them, and Tor over VPN can’t do anything about that, either. Again, we can’t emphasize enough that security and anonymity are paramount to those on dark websites. Your ISP and the government might not be able to view your activity when on the Tor Network, but they do know you are on the Tor Network, and that alone is enough to raise eyebrows.
Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user. In some countries, evading government restrictions to seek new political ideologies is punishable. For example, China uses the Great Firewall to block access to Western sites. Accessing blocked content can result in being placed on a watch list or imprisonment.
To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web. Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged.
Download Tor Browser
As a result, it not only focuses on the UK but also provides worldwide news. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. Analytics Insight is an award-winning tech news publication that delivers in-depth insights into the major technology trends that impact the markets. The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation. Always conduct your own research or check with certified experts before investing, and be prepared for potential losses. Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors.

By distributing communication over several nodes, it obscures the user’s IP address. People often have bad feelings about the dark web, but not everything on it is illegal or dangerous. In fact, journalists, privacy advocates and academics use it every day to protect their identities and get to material that has not been blocked. This page may contain sensitive or adult content that’s not for everyone.
In fact, a recent judgment by the US Supreme Court denoted that simply using Tor was sufficient probable cause for law enforcement to search and seize any computer around the world. The dark web, an even more puzzling sublayer, exists within this hidden world. It’s designed as an environment to elude detection, where site owners and visitors hide their identities.
How To Access Dark Web Safely In 2024
The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. So, anyone wishing to access it should create an account first. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article). Though people usually think of dark websites as the wrong online place, that’s not the complete truth.
How Can Beginners Detect And Analyze PDF Malware Step By Step?
This provides a full month’s access to all of the features of the #1 VPN for the Dark Web. This is an excellent way for Dark Web users to provide additional privacy protection when accessing the Dark Web. Darknet markets facilitate transactions for illegal goods and services.
The Dark Web remains a shrouded corner of the internet—an enigmatic space where privacy, free speech, criminality, and censorship resistance intersect. The moderation team likely has no connections or relationships with individuals or organizations who sell, buy, and post in r/darknet, have a connection to r/darknet, or to the dark web. We cannot help you resolve conflicts stemming from your private dealings with people inside or outside of this subreddit. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails. This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down.
You don’t even need to use Tor Browser, but keep in mind other browsers can still pass identifying information through the network. Alternatively, there’s IPVanish who claim to be the world’s number one VPN for Tor and comes highly recommended, you can save 60% on the annual plan here. Another vital precaution is to ensure that your .onion URLs are correct. Onion URLs generally contain a string of seemingly random letters and numbers.



