
Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation. Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. Over an eight-month period, a developer working for an affiliate marketer scraped customer data, including usernames and mobile numbers, from the Alibaba Chinese shopping website, Taobao, using crawler software that he created. It appears the developer and his employer were collecting the information for their own use and did not sell it on the black market, although both were sentenced to three years in prison. So, here it is – an up-to-date list of the 20 biggest data breaches in recent history, including details of those affected, who was responsible, and how the companies responded.
Northern Lights Forecasts, Alerts, And Geomagnetic Storm Warnings – Live Updates
These tools safely check your email address against recent data breaches to see if your passwords or personal information have been leaked. You can also use a free digital footprint checker to see what sensitive information is easily available to hackers and scammers online. Some services may offer additional features, such as dark web surveillance and tools to safeguard children. There are free credit monitoring services that come with more limited features. It has built a reputation for being a reliable source of stolen credit card data and PII.
In The Pok�mon Department
- Fill out the form or reach out to us at email protected to get access.
- All of this has made it one of the most reliable markets still active in 2025.
- Any bankruptcies or negative judgments will also be noted, as will any statements of dispute you may have filed.
- In some situations, your liability could depend on how long you take to report the fraud.
Credit monitoring services protect your personal information from cybercriminals and raise an alert if your identity has been compromised. Freshtools is a unique marketplace in that it does not only provide the stolen data, but it allows criminals to purchase MaaS which can cause further damage to the victims. It is one of the most active and up to date markets and always provides new and updated malware and data. By monitoring dark web markets, we often discover data breaches before they’re publicly reported. In this post, we’ll cover how credit card fraud operates on the dark web, how criminals obtain and trade card data, and cover some essential prevention strategies. Credit card skimmers are devices that threat actors use to steal your credit card information.
Russian Market

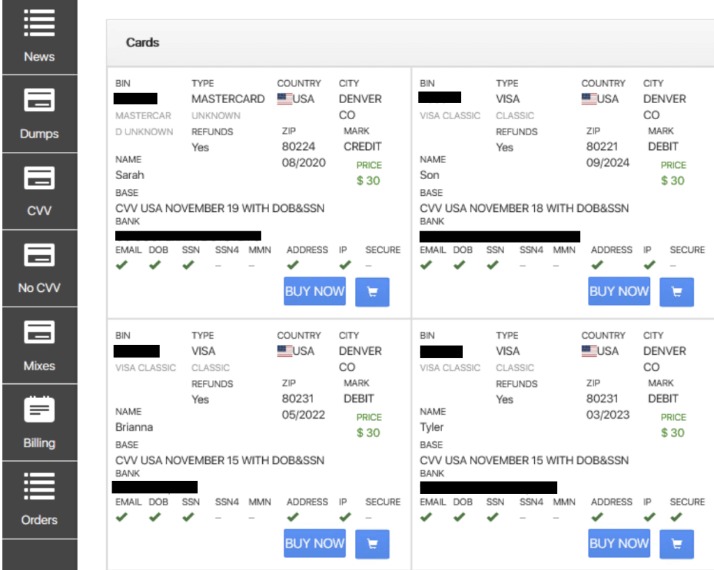
Stolen credit cards are used to cash them out or make purchases that can be resold. Full or partial credit card details are commonly sold on the dark web, including BIN numbers, credit card numbers, expiration dates, and CVV numbers. All of these features, its competitive pricing, along with the volume of credit card information listings, make Real and Rare one of the prime sites to trade credit card information online. Many of us think that the only way that scammers can steal personal card details is by stealing the physical card itself.
Instead, accessing the Dark Web requires a specialized browser called Tor, which hides users’ locations and identities. The downside to using free tools is that they only scratch the surface. To find out the true extent of how much of your personal information has been leaked, you need a stronger and more continuous monitoring method . LifeLock plans automatically monitor the dark web for your email address, but you can add your bank account numbers, driver’s license and other information, as well. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data. Russian Market has consistently remained one of the most popular and valuable data stores on the dark web.
Best For Dark Web Monitoring: LifeLock By Norton

You have to freeze your reports separately at each credit bureau, which you can do online, over the phone or by mail. Additionally, you might be able to use a password manager to create a passkey for your accounts. One of the first things you can do is change any potentially compromised passwords to help keep people from taking over your accounts. If you use the same password—or similar password variations—for multiple accounts, you may want to change the other accounts’ passwords as well. Aura’s service does not monitor for all content or your child’s behavior in real time. If you don’t feel safer after signing up for Aura, we offer a 60-day money-back guarantee on all annual plans — no questions asked.
These systems can often identify when stolen card data is being tested before major fraud attempts begin. If you’re connected to a public WiFi network, avoid making any purchases online while you’re connected to the network as this could place your financial data at risk. Instead, wait to make an online purchase until you’re on your home’s WiFi network. If you have to make a purchase immediately, create a password-protected hotspot to connect to your phone’s cellular data instead. Strong passwords and Multi-Factor Authentication (MFA) help keep your online accounts secure from compromise.
Hearing Hubble
Anyone can register for CreditWise or Chase Credit Journey, whether they’re a cardholder or not. Cybercriminals moved laterally through their ingress points before stealing credentials that allowed them to query its databases, systematically siphoning off stolen data. US authorities charged four named members of the Chinese military with masterminding the hack. Attackers broke into Equifax’s systems between May and July 2017 by taking advantage of an unpatched Apache Struts vulnerability to hack into the credit reference agency’s dispute resolution portal. Patches for the exploited vulnerability had been available since March 2017, months before the attack. Struts is a popular framework for creating Java-based web applications.
Just in the last 3 months millions of unique credit card credentials have circulated across the deep and dark web. Microsoft today released updates to fix more than 100 security flaws in its Windows operating systems and other software. At least 13 of the bugs received Microsoft’s most-dire “critical” rating, meaning they could be abused by malware or malcontents to gain remote access to a Windows system with little or no help from users. That phishing spree netted Urban and others access to more than 130 companies, including Twilio, LastPass, DoorDash, MailChimp, and Plex. The government says the group used that access to steal proprietary company data and customer information, and that members also phished people to steal millions of dollars worth of cryptocurrency.
Data That Was Found And Suggested Next Steps
Keep an eye on your bank, investment, crypto and credit card accounts for any unusual activity. By observing how threat actors advertise and price different types of card data, we can identify which security measures they’re successfully bypassing and which ones are still effective. While consumers are typically protected from direct financial losses, dealing with credit card fraud is incredibly disruptive. This type of malware silently infect payment terminals and exfiltrate card data in real-time. She combines her background in digital marketing from DePaul University with a passion for cybersecurity to create content that helps people and businesses stay secure.
Leveraging Outseer FraudAction Compromised Credit Card Feeds

Look online or contact your carrier to find out what you need to do to enable them. You can check to see if and what information is out there with a free dark web scan. And while there might not be a simple way to get your information removed from the dark web, you can take measures to protect your accounts and identity. Criminals can use this information in a variety of ways, such as impersonating you, creating a fake identity, opening credit accounts in your name or getting a medical procedure using your insurance.
To freeze your credit, you need to contact each of the three major credit bureaus individually — Experian, Equifax, and TransUnion. To check for more sensitive leaked information — such as your Social Security number (SSN), phone number, or scans of your physical IDs — you need to sign up for a dedicated Dark Web monitoring service. You’ll only find out if passwords and other saved data have been leaked. While searching for your information on Dark Web marketplaces might be tempting, it’s not worth the risk. If your identity is compromised, ID Shield’s private investigators can help restore it to its pre-breach status so you’re not on the hook for any financial damage caused by cybercriminals.
- Therefore, it’s better to minimize your digital footprint as much as possible to make yourself a less vulnerable target.
- If you notice a new account was opened in your name, the company can also help you close the account.
- Opinions expressed here are author’s alone, not those of any bank, credit card issuer or other company, and have not been reviewed, approved or otherwise endorsed by any of these entities, unless sponsorship is explicitly indicated.
- Additionally, securing transactions with a 3-D Secure ACS (Access Control Server) solution plays a pivotal role in bolstering the overall fraud prevention strategy.
- Payment information is stolen in a variety of ways before it ends up on the dark web.
- He showed off his account on Deliveroo, a British online food delivery company, where he had 65 credit cards saved.
These paid services provide continuous surveillance — scanning new Dark Web databases for your most sensitive information and alerting you if your data is found. Most Dark Web monitoring services also come bundled with identity theft protection, credit monitoring, and digital security tools such as antivirus and a password manager. PrivacyGuard’s top-tier plan, Total Protection, combines the best of credit monitoring and identity theft protection, including daily three-bureau monitoring, monthly credit score tracking, dark web scanning and identity theft insurance. Cybercriminal groups peddling sophisticated phishing kits that convert stolen card data into mobile wallets have recently shifted their focus to targeting customers of brokerage services, new research shows. Financial institutions can proactively strengthen their defences by integrating intelligence derived from FraudAction.
This Avdeev surname came up in a lengthy conversation with Lockbitsupp, the leader of the rapacious and destructive ransomware affiliate group Lockbit. The conversation took place in February 2024, when Lockbitsupp asked for help identifying Toha’s real-life identity. Since the Europol announcement, the XSS forum resurfaced at a new address on the deep web (reachable only via the anonymity network Tor). But from reviewing the recent posts, there appears to be little consensus among longtime members about the identity of the now-detained XSS administrator. The May 2025 DDoS was launched by an IoT botnet called Aisuru, which I discovered was operated by a 21-year-old man in Brazil named Kaike Southier Leite.
“This demo brought me right back, blending elements of real-time strategy, RPGs and first-person play into something very real.” Get expert tips, strategies, news and everything else you need to maximize your money, right to your inbox. Your name, current and previous addresses, phone number, Social Security number, date of birth, and current and previous employers are also listed on your credit history. This is the Songstress Style Holowear for Gardevoir which is obtained by through a spceial event Treasure Chest. This Holowear is a new rarity of Holowear which includes animations for Moves, movement, Unite Moves and more. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests.



