
This means you can store information for all your cards in oneconvenient location, making it easy to switch between cards whenpurchasing. Thefact that credit card (CC) information is already stored on thedevice and added to the wallet immediately triggered the attention ofcybercriminals. They started to design new techniques and tools toleverage NFC and mobile wallets to perform illegal transactions andsteal money from victims. Hundreds of millions of payment card details have been stolen from online retailers, banks and payment companies before being sold on online marketplaces such as UniCC.
Traditional payments typically require some Cardholder Verification Method (CVM) such as PIN or signature. For low-value contactless payments below the “Contactless CVM limit,” no CVM is required—the consumer can simply Tap & Go. TheZ-NFC behaves like a malware loader, using advanced Android packing,native code injection, and NFC emulation to conceal and executepayloads.
Top Cybersecurity Discord Servers To Join

Experian websites have been designed to support modern, up-to-date internet browsers. This stolen information is exploited by threat actors for financial gain through unauthorized charges, account takeover, and identity theft. The resulting financial loss is tremendous not only for the individual victim but also for the financial provider and any involved organizations. Crucially, she also outlines what service providers—including telcos, financial services, and insurers—can do to help protect consumers from carding in today’s shifting cyber threat landscape.
Steps To Take If Your Credit Card Information Is On The Dark Web
A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become. All content provided on Web Design Booth is for informational purposes only and does not constitute professional advice. We strive for accuracy and authority, but it is recommended to consult with qualified professionals before making decisions based on our content. Web Design Booth may receive compensation from third-party advertisers, which does not influence our editorial content. Abraham Lebsack is a seasoned writer with a keen interest in finance and insurance. Credit card prices also vary depending on the brand, with American Express being worth the most at 5.13 cents per dollar.
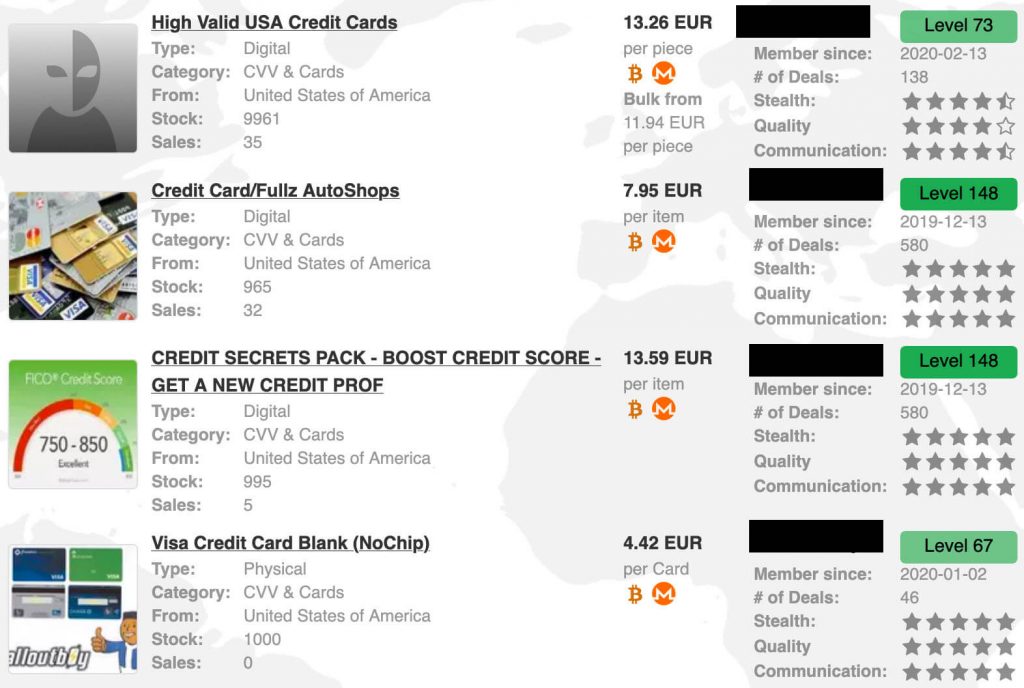
It is understood that the data included such highly sensitive information as the primary account number of the credit cards concerned, along with expiration dates and the card verification value, CVV2, security code. But that’s not all; there are also cardholder details such as their full name, address, date of birth and telephone number as well as email address. Pretty much everything you would need to commit credit card fraud or launch phishing attacks against the cardholder. Dark web credit card numbers are stolen card details sold on hidden websites. Some vendors offer a “complete package” known as “Fullz”, which includes full personal details as well as financial details like bank account information or social security numbers. Some threat actors offer a “complete package” known as “Fullz”, which includes full personal details and financial information like bank account details or social security numbers.
- In fact, the overwhelming majority of leaked credit cards in past months originate from Telegram channels.
- Another method employed is card skimming, where criminals install hidden devices on legitimate payment terminals or ATMs to capture card details for later use.
- Eventhough individual transactions may be small, the cumulative lossescan be substantial when applied at scale.
- TheZ-NFC behaves like a malware loader, using advanced Android packing,native code injection, and NFC emulation to conceal and executepayloads.
- Our platform can detect any suspicious mentions about organizations, or stolen payment information to give as much time as possible to prepare for data breaches.
Why Monitor Deep And Dark Web Credit Card Sites?
Ouranalysts from the HUNTER unit identified a group on Telegram offeringthe Z-NFC tool for sale to facilitate fraudulent transactions. Another tool, called King NFC, was previously marketed on the Dark Web as an alternative. Notably, the Telegram channels offering it are named X-NFC, which may create some confusion.
Responding To Detected Credit Card Fraud
Thank you for joining us on this exploration of credit card transactions on the Dark Web. Stay vigilant, protect yourself and others, and make ethical decisions when navigating the vast landscape of the internet. Enhance your online security by using robust passwords, enabling two-factor authentication, and being cautious with sharing personal details. The dark web, shrouded in anonymity and lacking regulation, serves as a breeding ground for criminal activity.

Trend Micro Cyber Risk Report
However, theseapps areavailable outside of Google Play and side-loaded, which is how theybypass all Android restrictions and can be used maliciously. The app utilizes Host Card Emulation (HCE) to mimic a physical ISO NFC smart card by registering a service that extends HostApduService. This allows it to respond to APDU command sequences just like a real card would. The payloads it handles are likely customizable, enabling users to define specific NFC responses — a capability that could potentially be used to spoof identity-based card systems.
How Does Information End Up On The Dark Web?

Other sellers offer discounts for buying multiple cards, while the cheapest card — with between US$700 and US$1,000 on it — can cost as little as US$80. Research by BitDefender has revealed the common prices for a range of illicit goods, from credit cards to credentials databases and more. Let this guide be your compass in a world where the dark web and digital innovation intersect.
Indicators Of Compromise In Threat Intelligence
After successful payment forlicense activation, it can be downloaded as an Android softwareinstallation package from a host generated by the Telegram bot. APDU (Application Protocol Data Unit) commands are the standardized communication units used between a smart card reader and a smart card. They are essential for executing operations on smart cards, such as reading data, writing data, or performing cryptographic functions. They all use HostCard Emulation (HCE) tomimic a physical ISO14443 NFC smart card byregistering a service that extends HostApduService. David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
How To Unblock Bajaj Finserv EMI Card Online
Instead, one must create strong and unique passwords using a password manager. Especially for your banks or financial accounts, the passwords must be strong and unique to that account only. Add your credit card number (along other personal details like email address, phone number, etc.) to the monitoring list. Scammers start by prompting users to download malware, which is often disguised as a harmless email attachment. Once it starts running on your machine, the malware collects data such as used keystrokes, browser history, and shopping habits. Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords.

Why Do Cybercriminals Hack PayPal Accounts?
A virtual card is a payment method you can use for online and over-the-phone purchases without revealing your actual card/account data to the merchant. The card contains a randomly generated 16-digit number with an expiration date and CVV. While the virtual card is tied to your real account, the merchant or a potential hacker can’t access your actual bank details.
By doing this, you can find your credentials for sale on the dark web and secure them before they are exploited. Fraudsters can use the stolen information for unauthorized transactions, identity theft, or resell the data on other platforms. The scale of this leak underscores the persistent vulnerabilities in global payment systems.
Use multifactor authentication to prevent threat actors from guessing at weak passwords, or getting into your systems with a brute force attack. MFA and strong password requirements will force your employees to use strong passwords and change them often. Once fraud is detected, a business must act immediately by contacting any customers who may have been impacted and contacting the payment processor to report the fraud. If the fraud involves multiple customers, notify them as soon as possible to inform them of the situation and to provide guidance on how to protect their personal and financial information. You may have never been to the dark web — but there’s a chance your credit card information has.



