Accessing the Dark Web safely in 2025 demands vigilance, preparation, and strict adherence to security best practices. By carefully following the safety procedures outlined in this guide, you minimize your risk of encountering malware, fraud, or legal troubles. Always remember, your safety online depends significantly on personal responsibility, informed decisions, and proactive application of security tips. Embrace these strategies to confidently navigate the Dark Web, preserving your privacy and security in an ever-evolving digital landscape. The dark web refers to websites that are not on the regular internet but are instead hidden in a private network that is only accessible using specialized web browsers, such as the Tor Browser.
Purchase Legal Goods Secretly
However, we strongly advise against using dark web marketplaces due to legal risks and the high likelihood of being scammed. A common misconception about the internet is that, once you open google, you can access anything and everything available online. In fact, only about 5-10% of the information on the internet is available through common browsers like Google Chrome or Mozilla Firefox, known as the ‘surface web’.
Download And Install The Tor Browser
- For beginners, this guide sets the foundation, and for further exploration, check out our Top Darknet Markets to dive deeper into this ecosystem.
- Fraudulent activities on the dark web include phishing scams, fake identity sales, and the sale of fake products.
- The internet providers and websites can still see that you’re using Tor as Tor node IPs are public.
- Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there.
- Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and trojan horses.
- Services such as Tumblers are also available on the dark web to help hide transactions.
Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be. Stay vigilant, trust your instincts, verify sources, and prioritize your security to make the most of the anonymity these networks provide. Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web.
Is The Dark Web Used For Illegal Purposes?
To access the Freenet-based dark web, you need to install the Freenet application. Some .onion dark websites are known to contain malware, and dangerous scripts designed to damage your computer, steal your information and identify you. Remember to uninstall any plug-ins you have before downloading, or prepare for them to be blocked – they can sometimes reveal your IP address, even if you’re using a VPN or onion router. Importantly, each node is representative of an additional layer of encryption. No node can track the complete path the traffic has taken, and more importantly, neither can anyone who finds it on the other side.
By equipping yourself with the right tools like Forest VPN and Tor or Onion browsers, you can explore safely and securely. Remember, the dark web isn’t just a den of iniquity; it’s a haven for privacy and free expression. Whether you’re a journalist, an activist, or simply curious, take the necessary precautions to remain secure. Enable two-factor authentication to avoid malicious actors accessing your accounts even if they get the correct username and password. Ensure your Tor browser is always up-to-date– automatic updates are enabled by default, but if turned off, you should manually update it regularly.
Why Do People Use The Dark Web?
Though these browsers are effective at serving up dark web search results, the experience is reminiscent of browsing the web in the late 1990s. Discovered pages are indexed in an extensive database and ranked based on numerous factors. When you search a term (or query) in a web browser, the search engine combs through the database to find relevant results and serves them up on SERPs. We also recommend using a virtual private network (VPN) such as NordVPN — the best dark web VPN — to add an extra layer of protection. You can read our NordVPN review for more information, or try it out yourself using the 30-day money-back guarantee.
Enhancing Your Security
There’s also little to no recourse to be had if you encounter any trouble there, because the dark web is a decentralized collection of websites hidden from search engines. It’s the side of the internet that’s used for transactions and conversations that need to stay anonymous. Unlike the surface web, which can be indexed by standard search engines, the dark web exists on encrypted networks and hosts websites with random, complex URLs.
Step-by-Step Guide: Access The Dark Web On Any Device
Users should refrain from clicking on unverified links and exercise discretion in revealing personal information. Drugs are typically sold using cryptocurrency to maintain anonymity, and the buyers and sellers are often difficult to trace. These markets operate similarly to physical drug markets but are hidden from law enforcement through the use of the Tor network. However, while using Tor itself is not illegal, some illegal activities can occur through the network, such as the distribution of child pornography or the sale of illegal drugs. It’s important to note that engaging in illegal activities is still illegal, even through the Tor network.
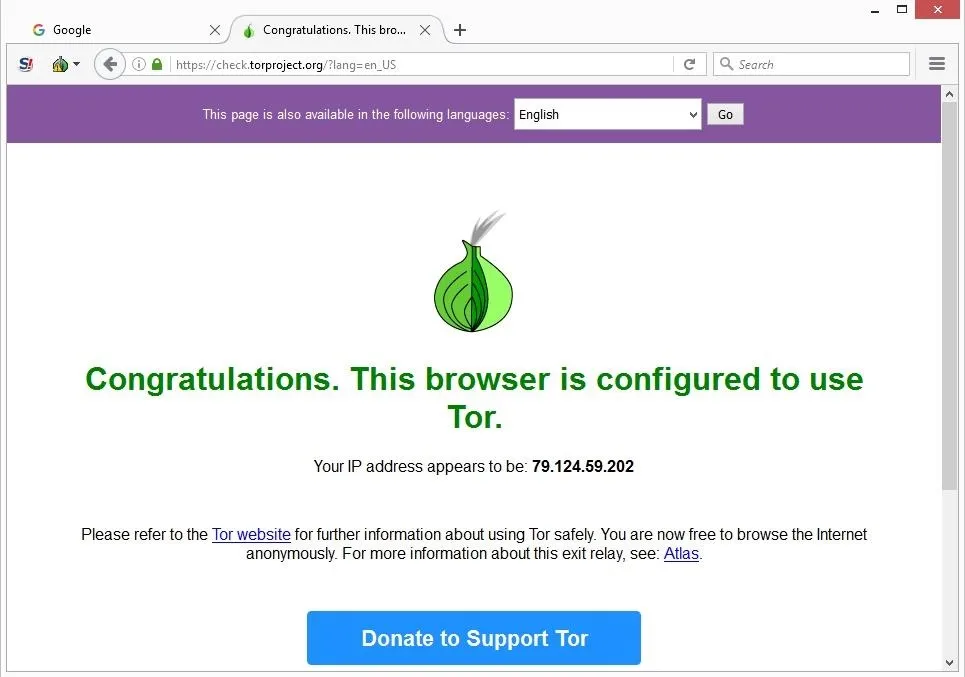
I2P’s most attractive angle is to access its own internal eepsites, which are its version of .onion sites. It is definitely a strong contender for the best, strongest, layered encrypted web browser. The browser routes your traffic through a global network of volunteer-run servers (sometimes called nodes), encrypting your data and masking your IP address multiple times. First and foremost, it\’s crucial to use the Tor browser, renowned for its privacy features. Users should exclusively download the Tor browser from the official torproject.org website to avoid potential security risks.
- At the time, the internet was still young, and tracking people was easy while staying anonymous was not.
- Understanding the differences and capabilities of various anonymity tools will help you make informed decisions about which networks best serve your needs.
- These corners are deliberately concealed from the public eye and require specialized tools and browsers to access, making it more difficult for the average person to explore.
- The following sections will explain how to access the dark web on different devices.
- The VPN connection will route your online activity through a different server, masking your activity from your internet service provider.
This layered encryption and anonymization make it difficult for authorities or outsiders to trace activities or identify participants. Because of these privacy features, the dark web remains a hidden but active part of the internet ecosystem. On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity. Despite its negative reputation, not all activity on the dark web is malicious; some users rely on it as a tool for freedom of expression or to circumvent restrictions.
VPN Over Tor

Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. The Dark Web offers users a level of anonymity that is not available on the Surface Web. By accessing websites through the Tor network, individuals can obscure their IP address and encrypt their traffic, preventing easy identification by third parties. This anonymity is particularly important for individuals living in repressive regimes or those concerned about government surveillance. Researchers and law enforcement professionals use the Dark Web to understand crime patterns and illegal activities by notorious groups to prevent these crimes from happening.

On the other hand, the deep web is the hidden part of the Internet that contains private or restricted content that is not indexed by search engines. Unlike the surface web, you can’t access deep web resources directly through a search engine; they require login credentials or special permissions. When accessing the dark web, the first step is to install a dark web-friendly browser on your computer. Unlike traditional browsers, this will route your internet traffic through an anonymizing network and mask your IP address.
Yes, simply accessing the dark web is legal in the United States. Downloading Tor or browsing .onion sites doesn’t break any laws on its own. Journalists, whistleblowers, and researchers often use it to protect their privacy or gather sensitive information.



