
This is why it’s crucial to always check for updated Ares links from trusted sources before attempting to access the marketplace. Ares implements end-to-end encryption for all communications and transactions. Your data remains secure from prying eyes, with automatic PGP encryption for sensitive information. Like the spartan phalanx, our community’s strength comes from unity and mutual protection. Every user, vendor, and administrator contributes to our collective security and success through disciplined adherence to our code.
Ares Darknet Users
Marketplaces that reach the top of the ecosystem, in terms of volume, user base, listings, and reputation, often become priority targets for law enforcement. Archetyp’s recent takedown followed this pattern and likely influenced Abacus’s trajectory. Discover how to explore darknet market links safely while ensuring your privacy and security. Whilst a great many products are sold, drugs dominate the numbers of listings, with the drugs including cannabis, MDMA, modafinil,108109110 LSD, cocaine, and designer drugs. The months and years after Silk Road’s closure were marked by a greatly increased number of shorter-lived markets as well as semi-regular law enforcement takedowns, hacks, scams and voluntary closures. Our bug bounty program incentivizes security researchers and ethical hackers to identify and report vulnerabilities in the platform.
🛡️ How Axis Intelligence Strengthens Cybersecurity
Malware is often disguised as legitimate listings, which unsuspecting users download, allowing cybercriminals to spy on activities or steal additional data. Escrow services act as intermediaries in high-value or higher-risk transactions. They help establish trust between buyers and sellers by holding payments until both parties confirm the deal’s completion.
Security Architecture
Furthermore, following Archetyp’s law enforcement seizure in June, 2025, many of its users flooded Abacus Market, leading to the latter’s largest ever monthly sales volume of USD 6.3 million in June 2025. Advanced search and filtering capabilities help users quickly find products and vendors that meet their specific requirements. The interface includes comprehensive vendor profiles, detailed product descriptions, and integrated communication tools that facilitate smooth transactions and customer support interactions. The login process requires users to decrypt a challenge message using their private PGP key, proving their identity without transmitting sensitive information. This method is significantly more secure than traditional password-based systems and provides protection against various attack vectors including credential stuffing and brute force attacks. Launched in 2020, Cypher Marketplace sells fraudulent documents, stolen credit cards, fake IDs, and malware.
Was Abacus Market Taken Down By Law Enforcement?
Some individuals and groups also leverage I2P, a peer-to-peer network designed for continuous routing within a decentralized environment. Beyond these specialized networks, users often connect through VPN services and proxy chains to further mask their physical locations. The Darknet is in constant flux, shaped by technological innovations, shifting user behaviors, and law enforcement crackdowns. To understand how these hidden marketplaces operate and why they continue to flourish, it’s useful to examine the primary trends that define today’s underground economy. While there are many sites that facilitate illegal activities, there are also legitimate sites that provide valuable resources, including educational materials and tools for privacy protection. While it’s true that it hosts illegal activities, it’s also a haven for those seeking privacy from prying eyes.
Darknet Markets Explained: Navigating The Hidden Web
The marketplace also thrives on its community-driven environment, where buyers leave detailed reviews that guide others toward trustworthy sellers. Over time, Ares has cultivated an identity that goes beyond mere transactions, promoting a sense of familiarity and interaction among its user base. Law enforcement crackdowns and exit scams remain constant threats, and the platform’s smaller user base means fewer alternatives if a trusted vendor disappears. Nevertheless, for those seeking a more controlled darknet experience, Ares offers a balance of reliability and anonymity in an unpredictable digital underworld. Engaging in illegal transactions exposes both buyers and sellers to legal repercussions.
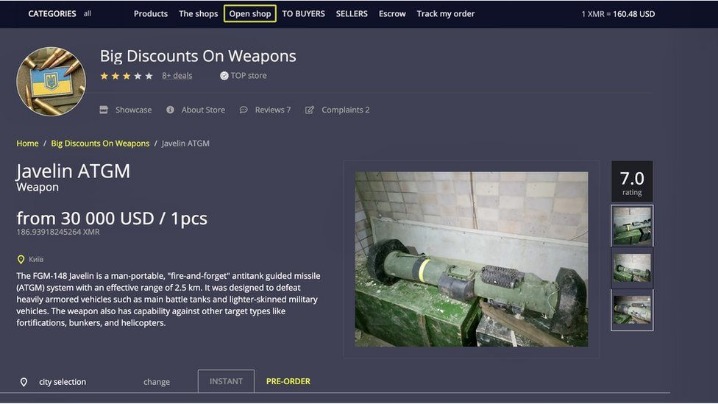
Vendors must provide comprehensive product information including specifications, origins, and any relevant safety information. Quality control measures must be implemented to ensure consistent product standards. Monero represents the gold standard for privacy-focused cryptocurrency transactions.
- It is one of the newest markets in the industry and was launched in the second half of 2021.
- Brian’s Club is one of the best place to buy stolen credit card info, including CVVs, dumps, and even full account packages without revealing your identity.
- By relying on encryption, pseudo-anonymous currencies, and network-level anonymity, they create a false sense of safety, drawing in both buyers and sellers.
- Welcome to Ares Darknet Market, the official hidden sanctuary where warriors of the digital age gather.
Final Verdict- Is Ares Market A Good Darknet Market?
Personal data breaches pose a serious risk to darknet participants. Account compromises can expose users’ pseudonymous identities, while crypto wallet theft remains a prevalent threat when hackers intercept private keys. De-anonymization of both buyers and sellers can happen through advanced tracking techniques, such as malicious software implants or poor operational security practices.
Russian Market has operated since 2019, specialising in stolen credentials, stealer logs, and remote desktop access. Threat reports consistently rank it among the top ten darknet sites Top 10 Dark Web Markets. Darknet markets operate within this hidden space, often hosting illegal activity, while the deep web primarily consists of everyday private or password-protected content.
The reason I rated it 3/5 for security is because it’s missing a few of my favourite features. Any and all your actions, including financial profits and losses due to scams will solely and exclusively be your own responsibility. The user journey proved smooth overall as an early-stage marketplace, validating ui/ux promises. This case was investigated as part of an FBI-led interagency Joint Criminal Opioid and Darknet Enforcement (J-CODE) operation.
To access them, copy and paste the hyperlinks provided into the Tor browser. If you use Ares Darknet Market for transactions, there’s a chance that it could be against the law in your location. The information here is for educational or research purposes and isn’t meant to encourage any illegal activities.
Darknet marketplaces in 2025 illustrate a resilient and evolving underground economy. Major active platforms include Abacus, Russian Market, BriansClub, and Exodus. Law enforcement takedowns, such as Archetyp, demonstrate both impact and adversary adaptation. For cybersecurity professionals, focusing on payment methods, vendor migration, and marketplace specialisation offers the most effective path to actionable intelligence.
- Cybercriminals exchange large troves of compromised login credentials, financial information, and personal identifiers, fueling subsequent attacks like phishing campaigns and account takeovers.
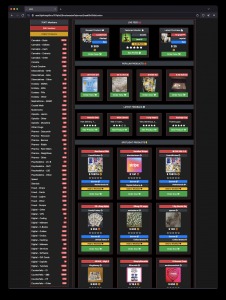
- These categories include drugs, fraud, hacking, counterfeits, and defense/intelligence, each with various subcategories.
- Users must ensure their activities comply with all applicable local, state, national, and international laws.
- So, if a “business opportunity” sounds too perfect, it probably is.
It is noteworthy to mention the multitude of essential features integrated within the menu bar, thereby facilitating user navigation. Downloading Tor for access, account creation only demanded providing a username, password, and PGP key. Mobile access may cause issues with functionality, formatting, or security features. This direct model reduces risks, speeds up payments, and preserves user autonomy. These links are cryptographically signed and verified by admin H0riz0n.
Hence, it should be the top priority to track these platforms and shut them down as quickly as possible. This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information. The cybercriminals trade even sensitive documents, such as medical records, passport information, and driver’s licenses. The marketplace supports multiple payment methods, including Bitcoin (BTC), Litecoin (LTC), and Cryptocheck. They add new batches of stolen data every other week, and there’s even a bidding system where buyers can place offers on new data batches as soon as they become available.



