
Some are designed for privacy-focused communication, while others provide marketplaces or forums for specific communities. Due to the unique nature of the Tor network, these best onion sites often thrive in anonymity, providing users with accessible services that prioritize privacy. Users can explore onion sites easily and search for content without having to know any specific onion links in advance. You’ll keep your identity private while getting results for various Tor websites, forums, and marketplaces. Onion sites are websites on the dark web that use the ‘.onion’ domain, accessible only through the Tor Browser. They provide enhanced privacy and anonymity by encrypting user data and masking IP addresses through multiple nodes, making it difficult to trace user activities.
How To Use These Tools Effectively
All users who create a new Webshare account automatically receive 10 free (shared datacenter) proxies + 1GB/month bandwidth to use for as long as they want, no credit card required. The user who signs up will get a free basic plan, and also have a 25% discount when upgrading. If you seek utmost privacy when surfing the web, the Tor browser is your best bet.
Step 1: Download And Install The Tor Browser
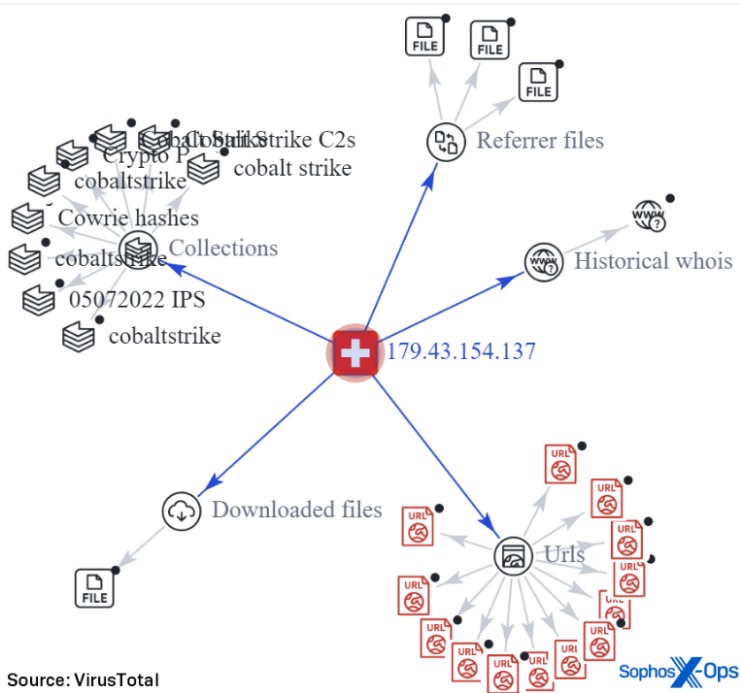
The files are automatically encrypted, and the sender’s IP is not logged. At this level, all features from the Tor Browser and other websites are enabled. While exploring the dark web can offer valuable privacy benefits, it’s crucial to understand common risks and how to manage them effectively. mark it means it has been verified as a scam service and it should be avoided. Ahmia promotes transparency by being open-source and allowing contributions.|Tor is a browser engineered for extra security and privacy, and can be used to navigate the normal, surface web as well as the dark web. It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. Offering books for free, shadow libraries face the morality question of copyright vs. access to information and knowledge. Just Another Library is one such service, with a wealth of books covering computer programming, science, and niche hobbies (sailors’ knots, anyone?).|These sites provide a level of privacy and anonymity unavailable on the surface web, offering content and goods that cannot be easily found through traditional online platforms. Tor Metrics is a set of tools and data provided by the Tor Project that offers insights into the performance, usage, and activity of the Tor ecosystem and its nodes. Besides monitoring and improving the network, the data can be used to detect possible censorship or attacks. Due to the privacy-forward ethos of the Tor project, Tor Metrics stresses that the data it collects must not undermine the anonymity or security of the network. The best dark web websites provide access to educational materials, host secure services, or bypass censorship. Dark web websites are hidden under layers of encryption that cloak user activity, which can be a boon to whistleblowers, activists, and others who don’t want anyone tracking their activity.|The platform includes a broad mix of content, from forums and marketplaces to privacy-focused resources, though it doesn’t filter out illegal sites, so caution is necessary. Being hidden doesn’t translate into being completely protected from the possibility of tracking, or, when it comes to illegal activities, of risk. However, it’s up to us to take control of our personal privacy in a world of bulk data collection, surveillance, and personalized ad tracking.}
We pay our bills online, check our bank statements, communicate via email, find information, and maintain a presence on social media. You might be surprised that the Tor Browser looks particularly, well, like a normal browser. Tor is basically a modified version of Mozilla Firefox, which is open-source and lends itself to modification. It looks, and behaves, and is, pretty much like any other browser you use to surf the web. You can use it to go to any websites you normally go to, like social media or news sites.
For example, you can use Signal as your daily messaging app– it has end-to-end encryption and collects minimal data unlike many other messaging apps. Enable two-factor authentication to avoid malicious actors accessing your accounts even if they get the correct username and password. Ensure your Tor browser is always up-to-date– automatic updates are enabled by default, but if turned off, you should manually update it regularly. Tor is slower than standard browsers because it routes your traffic through multiple servers. This routing, through at least three nodes distributed worldwide, introduces latency, especially when there’s congestion on specific nodes. The Tor browser routes your online requests through multiple nodes to obscure them from prying eyes.
Best Practices When Using onion Links And Mirrors
- The dark web is a hidden part of the internet that requires specialized software to access.
- Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS.
- In addition, know that while accessing the dark web is legal in most countries, engaging in illegal activities (buying or selling contraband, hacking services, etc.), is illegal everywhere.
- The publicizing of Snowden’s actions led to a global spike of interest in Tor and a resulting rapid expansion of the network’s user base.
- The only way to access the dark web is by using the correct browser and knowing the URLs of the pages you want to visit.
To maintain reliability, the Hidden Wiki is regularly updated by moderators and community members who verify the legitimacy of links, remove dead or malicious URLs, and add new, trusted resources. This ongoing maintenance ensures users can safely and confidently navigate the dark web with the help of the Hidden Wiki. Users turn to the Hidden Wiki because it simplifies navigation through the complex and often confusing dark web. Many people seek it out for privacy and anonymity, as the Tor network and the Hidden Wiki help mask identities and activities from surveillance. Furthermore, the Hidden Wiki plays a critical role in censorship resistance, providing uncensored content and services that might be blocked on the surface web. Your safety on the dark web depends more on cautious browsing habits than any single security tool.
Who Created Tor?
While some .onion sites provide essential services like secure communication and censorship-free journalism, others spread malware or run scams. With this in mind, finding verified links is crucial for avoiding threats on the dark web. You can tell you’re on the dark web if you’re accessing websites with .onion addresses on the Tor Browser or a similar anonymity network.
How Are Dark Web Links Different From Regular Web Links?
The CIA is contactable on the dark web, providing a completely anonymous way to get in touch with them. However, if you’re communicating with state intelligence agencies, you should use Tor alongside a VPN for maximum privacy. Otherwise, the first node in the onion relay system sees your real IP address, which can be used to locate you and unveil your identity. The New York Times can also be anonymously accessed via the dark web. Some locations block access to the site, so the New York Times began hosting on the dark web to unblock links to their news and make it accessible to everyone around the world. Borderless news reporting and uncensored media are among the most important and practical uses for the dark web.
Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together. The .onion site has thousands of downloadable comic books ranging from niche to mainstream. As with the Imperial Library, you should be aware of copyright infringement. It allows you to search for images, maps, files, videos, social media posts, and more.
How Can I Increase Security While Using Tor?
We continuously monitor and update our directories to minimize risks and ensure users have access to trusted, legitimate sites. Our goal is to empower you with reliable information and resources, making your dark web experience as secure and informed as possible. The Tor Browser looks and feels similar to a regular web browser but is configured to prioritize privacy and security by default.
Likewise, some websites allow Tor, but with frequent Captchas that can be annoying. You can use a VPN if you’re in a country that restricts or heavily monitors Tor usage. You can also use it if you don’t want your network administrator or ISP to be aware of your Tor usage.

It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities. A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely.
This encryption and relaying of your browsing data prevents anyone who is watching from detecting which websites you are visiting. For example, state-level actors can execute traffic correlation attacks, wherein they monitor both incoming traffic at the entry nodes and outgoing traffic at the exit nodes. By observing these patterns, they can link a Tor user’s request to a server and reveal their intended destination. Tor traffic is decrypted at the exit node, which opens a vulnerability for malicious actors to inject malware or intercept traffic.
Choose a trustworthy VPN service that has a strict no-logs policy and supports connection without DNS leaks. Avoid free VPNs as they often lack adequate security or monetize user data. WhiteHouse Market has earned a reputation for its robust vendor verification and user-friendly design. It employs escrow services and PGP encryption for communications, significantly reducing the risk of scams.



